Note: Please wait for the Flash to load. As this is my first attempt to create a flash based blog. Bear with me for all the issues that you observe. Thank you for your patience.
Tuesday, 15 October 2013
Tuesday, 12 March 2013
Oracle Access Manager ( OAM ), Oracle Adaptive Access Manager ( OAAM ) and Oracle Identity Manager ( OIM ) Integration ( 11gR2 )
It has been very long time since I wrote anything on this blog. This time I am trying to cover up one of the most painful topics "OAM-OIM-OAAM Integration".
I have tried to take screenshots of the steps that needs to be followed. Most of them are self explanatory but I added text where ever possible.
Note: This is not Oracle's official document. You should refer to the Integration Guide provided by Oracle for production implementation. Also, there is no guarantee that information provided in this blog is error free. Also, few assumptions are made that WLS is installed and configured, required database schemas are created using correct RCU and the domain for OAM/OIM/OAAM has been created. All the three products are part of same domain.
I have tried to take screenshots of the steps that needs to be followed. Most of them are self explanatory but I added text where ever possible.
Note: This is not Oracle's official document. You should refer to the Integration Guide provided by Oracle for production implementation. Also, there is no guarantee that information provided in this blog is error free. Also, few assumptions are made that WLS is installed and configured, required database schemas are created using correct RCU and the domain for OAM/OIM/OAAM has been created. All the three products are part of same domain.
- Before you start your Admin Server or OAM Managed server first time. You have to execute the below mentioned commands related to OPSS security store. OIM has not yet been configured in this domain. The domain was created by selecting OIM product but the required config.sh is not executed till the steps show later.






- This is exception can be ignored.

- We are going to start the integration steps. The first step is the set the required environment variables and execute idmconfigtool with required properties files.

- Create the properties files for each activity. We will be creating properties file for preConfig Identity Store, prepare Identity Store, OAM Configuration for integration and OIM configuration for integration.

- Prepare Identity Store properties file.

- OAM configuration properties file for integration.


- OIM configuration properties file for integration.

- Execute idmconfigtool for preconfig identity store to create required schemas in LDAP server.


- Once schema extension is completed prepare identity store for OAM.


- Once OAM is completed prepare identity store for OIM.


- Now start the config wizard to configure OIM.


- Provide database connection details

- Provide values for keystore and the front ending URL. Also, password for xelsysadm user. Make sure you have selected "Enable LDAP Sync"

- I am using OID LDAP server. Hence, I have provided required parameters for it. If you have any other LDAP server follow appropriate steps per Oracle Documentation on how to enable LDAP Sync.





- Once configuration is completed successfully restart all your servers.


- Configure the properties for POST LDAP Sync execution steps.


- Set required environment variables.
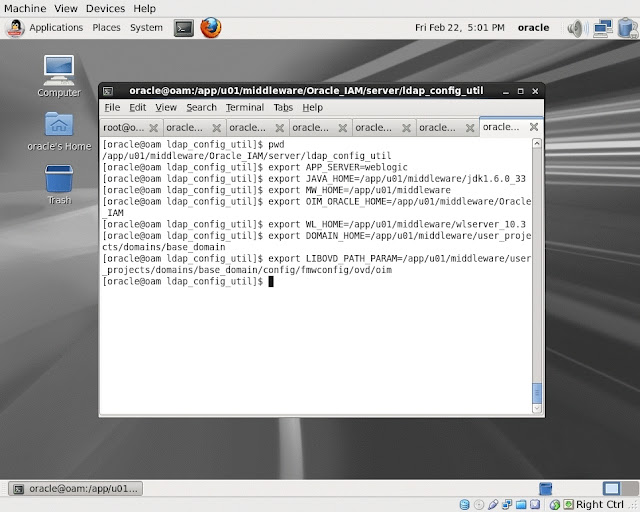
- Update XEL_HOME parameter in the file setEnv.sh.

- Execute the utility LDAPConfigPostSetup.sh

- Now go back to idmconfigtool. Make sure you have required environment variables set. Execute the tool for configuring OAM for integration.


- Make sure you have required environment variables set. Execute the tool for configuring OIM for integration



- Update password of IAMSuiteAgent.

- Update the password of IAMSuite Agent in the WebLogic Console's Provider configuration.

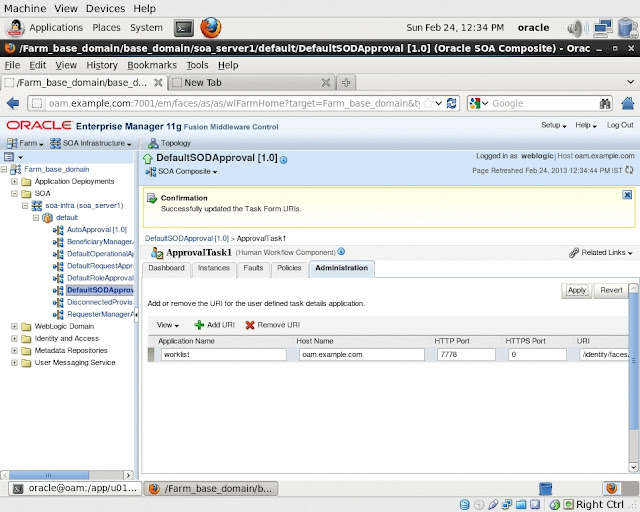
- Modify the SOA Composite configuration to use HTTP Port of reverse proxy web server.







- OAM and OIM integration steps are completed. Now we are starting the OAM-OIM-OAAM integration steps. After creating a new user in OIM if you are unable to login to OAM's protected resource. Make sure that you have correct configuration in the User Identity Store. We will review it later before we try to access a protected resource.

-
- Import the snapshot provided with OAAM. This snapshot will automatically provide required Rules, KBA, etc. related configuration.






- Preparing for OAM and OAAM integration.

- Execute the WLST command to create required Keystore file.

- Execute the highlighted WLST command.

- Copy the CLI directory from Oracle Home of OAAM. Edit the file oaam_cli.properties.



- Set required parameters and execute setupOAMTAPIntegration.sh.





- Configuration is successful restart all your servers.

- Configure Challenge Parameters in OAM console for TAPScheme to include parameter "MatchLDAPAttribute=uid".

- Modify System Properties in OIM to disable Challenge Questions, update the Forgot Password URL etc. in the OIM's Administration console.







- Login to OAAM's Admin Console and modify parameters shown in the screenshots.





- Login to EM Console and navigate to Credential configuration. Add a new Key in the OAAM's MAP. Provide xelsysadm username and password.

- Login to OAM console and update the Load Balancing configuration as per your environment.

- Create a new Authentication Policy to protect a resource with TAP Scheme.

- If you notice the below mentioned error in the logs. It means that you have to manually add one attribute in OID's schema and attach it to an Objectclass in OID.





- Make sure that User Identity Store created by idmconfigtool has correct parameters as shown in the screenshot. User Name Attribute should have value uid.

- Login to OIM Console. Create a new user to test if the configuration is working fine or not.

- Try to access a protected resource with OAAM's Authentication Scheme.

- Provide Username.

- Provide password and you would be redirected to change password page.

- Change the current password. Once it is changed you will be redirected to configure Challenge questions for Forgot Password Scenario.


- Select the Device configuration you would like to use.

- Set required Questions and Answers.

- Authentication has completed and required SSO Cookies are set.

- Now we are testing the forgot password scenario.

- Instead of providing the passoword. Click on Forgot your password URL.

- Answer all questions.



- Finally you land on password change page. Provide new Password and Confirm New password.

- Now you are redirected to the protected resource.

Subscribe to:
Comments (Atom)
